Integrations
/Microsoft Azure
Microsoft Azure
You may want to integrate with Microsoft Azure Active Directory (AD) if:
- You want to let users (such as employees in your company) log into your application from an Azure AD controlled by you or your organization.
- You want to let users from other companies' Azure ADs into your application. (You may want to set up those external directories as different connections.)
Steps
To connect OBS ERP to Microsoft Azure AD, you must:
- Set up OBS EPR in the Microsoft Azure portal
- Create an enterprise connection in OBS ERP
- Test the connection.
Microsoft Azure Account
Before proceeding, you will need a valid Microsoft Azure account and must have your own Microsoft Azure AD directory for which you are a Global administrator.
If you don't have a Microsoft Azure account, you can sign up for free, and set up an Azure AD directory by following Microsoft's Quickstart: Create a new tenant in Azure Active Directory .
Set up your app in the Microsoft Azure portal
To allow users to log in using a Microsoft Azure Active Directory account, you must register your application in the Microsoft Azure portal.
Before proceeding, you must have already set up your own Microsoft Azure AD directory for which you are a Global administrator.
Register a new application
To learn how to register your application with Azure AD, follow Microsoft's Quickstart: Register an application with the Microsoft identity platform .
Create a client secret
To learn how to create a client secret, follow Microsoft's Quickstart: Configure a client application to access web APIs .
Add permissions
To learn how to add permissions, follow Microsoft's Quickstart: Configure a client application to access web APIs .
Token configuration
Make sure the following claims are on the list:
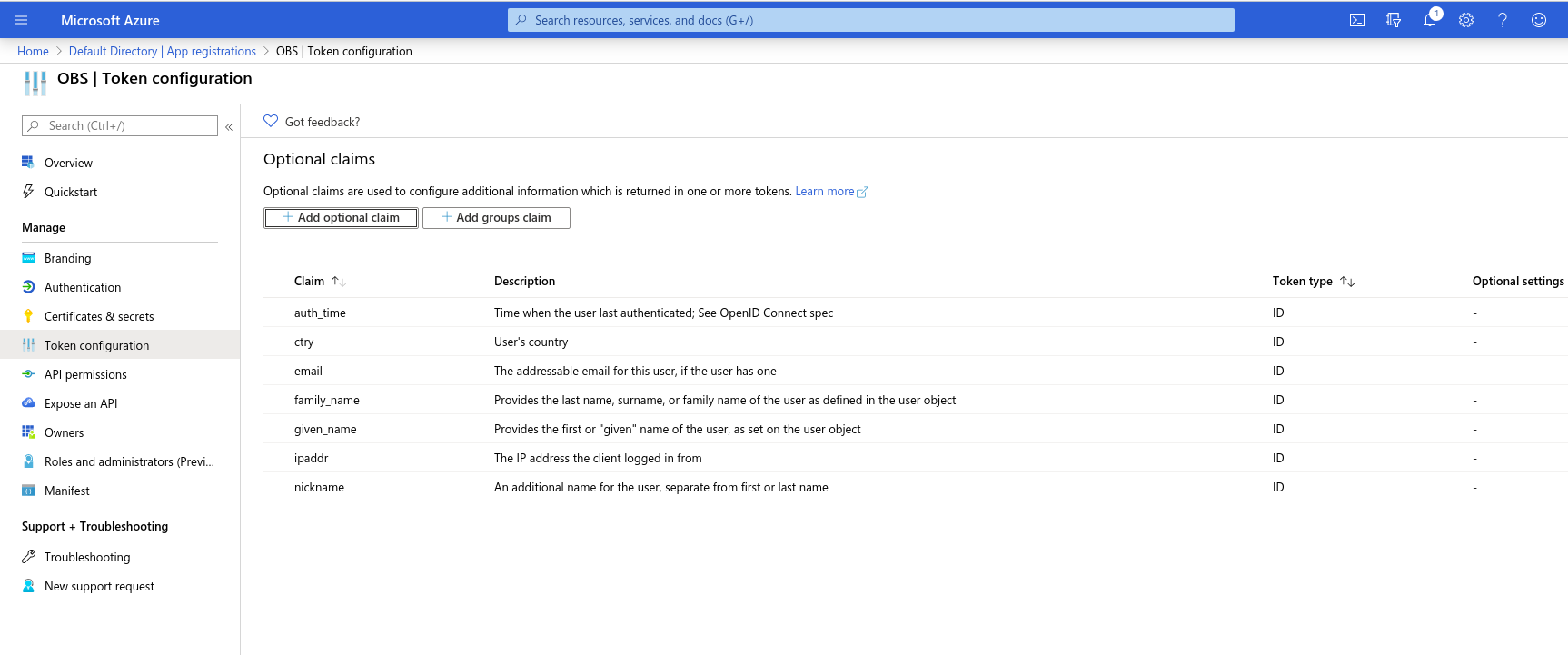
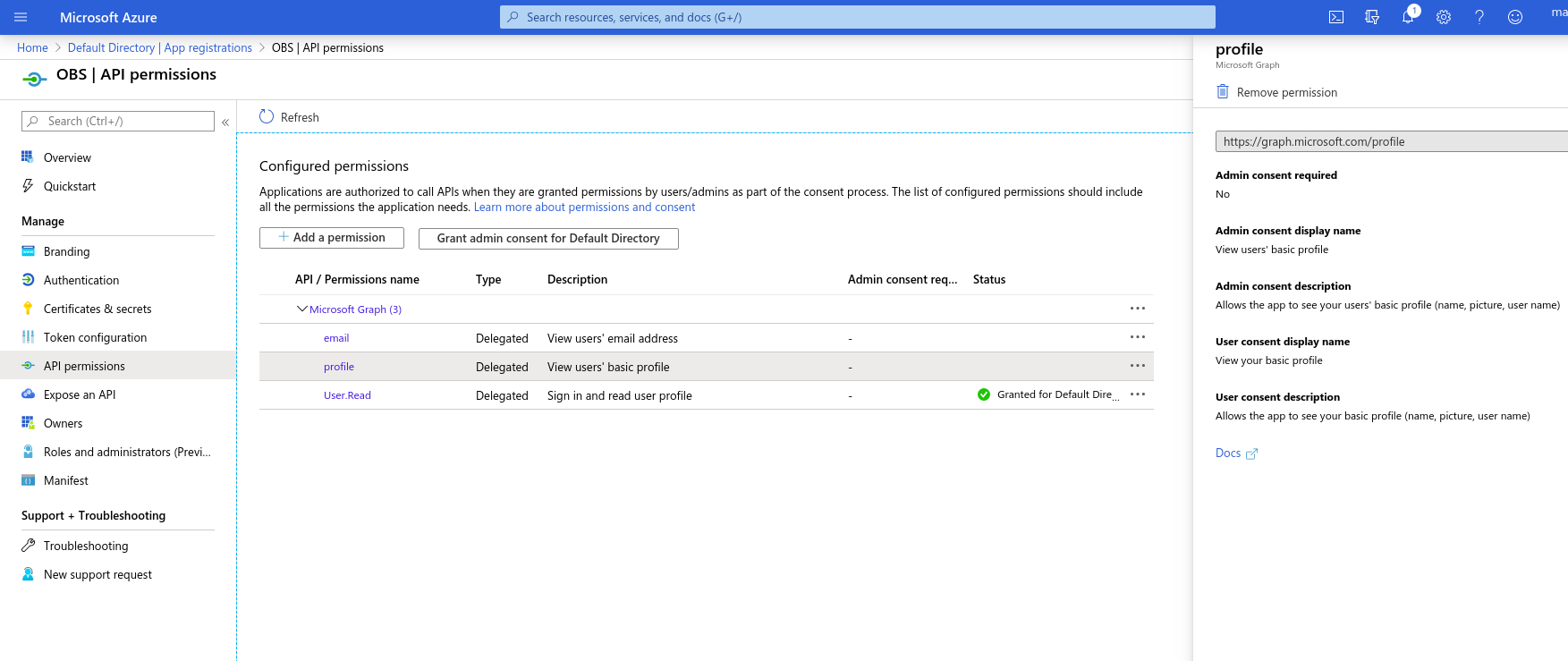
API Permissions
The following permissions should be on the list:
Create an Enterprise Connection in OBS ERP
Open "Administration → Settings → Preferences" and add the following variables:
| Description | Key | Value |
|---|---|---|
| MS Azure Resource | AzureResource | {resource} e.g. api://2d4170c2-09ef-4532-9266-4ea9ec46c9bf |
| MS Azure Directory Tenant ID | AzureTenantID | {tenant} e.g. ab00192f-94a1-4f17-bc3a-062b03ae3c43 |
| Token URL in MS Azure | AzureTokenURL | https://login.microsoftonline.com/{tenant}/oauth2/token |
| Authorization URL in MS Azure | AzureAuthURL | https://login.microsoftonline.com/{tenant}/oauth2/authorize |
| Application ID in MS Azure | AzureClientID | {application_id} e.g. 2d4170c2-09ef-4532-9266-4ea9ec46c9bf |
| MS Azure Client Secret | AzureClientSecret | {secret} e.g. QlpXFFeqy5x-l5z1uNgbZInSEfn_oBf= |
